Home » Articles posted by Agus M Soleh
Author Archives: Agus M Soleh
Ilustrasi Indeks Kepuasan Masyarakat (Paramadina)
Materi Ilustrasi Perhitungan Index Gabungan (Indeks Kepuasan Masyarakat):
Indeks Gabungan (Paramadina)
Materi: Paparan
Reference:
https://www.oecd.org/els/soc/handbookonconstructingcompositeindicatorsmethodologyanduserguide.htm -> Handbook (PDF)
How To Secure Apache with Let’s Encrypt on Ubuntu 18.04
Introduction
Let’s Encrypt is a Certificate Authority (CA) that provides an easy way to obtain and install free TLS/SSL certificates, thereby enabling encrypted HTTPS on web servers. It simplifies the process by providing a software client, Certbot, that attempts to automate most (if not all) of the required steps. Currently, the entire process of obtaining and installing a certificate is fully automated on both Apache and Nginx.
In this tutorial, you will use Certbot to obtain a free SSL certificate for Apache on Ubuntu 18.04 and set up your certificate to renew automatically.
This tutorial will use a separate Apache virtual host file instead of the default configuration file. We recommend creating new Apache virtual host files for each domain because it helps to avoid common mistakes and maintains the default files as a fallback configuration.
Prerequisites
To follow this tutorial, you will need:
- One Ubuntu 18.04 server set up by following this initial server setup for Ubuntu 18.04 tutorial, including a sudo non-root user and a firewall.
- A fully registered domain name. This tutorial will use your_domain as an example throughout. You can purchase a domain name on Namecheap, get one for free on Freenom, or use the domain registrar of your choice.
- Both of the following DNS records set up for your server. You can follow this introduction to DigitalOcean DNS for details on how to add them.
- An A record with
your_domainpointing to your server’s public IP address. - An A record with
www.your_domainpointing to your server’s public IP address.
- An A record with
- Apache installed by following How To Install Apache on Ubuntu 18.04. Be sure that you have a virtual host file for your domain. This tutorial will use
/etc/apache2/sites-available/your_domain.confas an example.
Step 1 — Installing Certbot
The first step to using Let’s Encrypt to obtain an SSL certificate is to install the Certbot software on your server.
Certbot is in very active development, so the Certbot packages provided by Ubuntu tend to be outdated. However, the Certbot developers maintain a Ubuntu software repository with up-to-date versions, so we’ll use that repository instead.
First, add the repository:
You’ll need to press ENTER to accept.
Install Certbot’s Apache package with apt:
Certbot is now ready to use, but in order for it to configure SSL for Apache, we need to verify some of Apache’s configuration.
Step 2 — Set Up the SSL Certificate
Certbot needs to be able to find the correct virtual host in your Apache configuration for it to automatically configure SSL. Specifically, it does this by looking for a ServerName directive that matches the domain you request a certificate for.
If you followed the virtual host set up step in the Apache installation tutorial, you should have a VirtualHost block for your domain at /etc/apache2/sites-available/your_domain.com.conf with the ServerName directive already set appropriately.
To check, open the virtual host file for your domain using nano or your favorite text editor:
Find the existing ServerName line. It should look like this:
If it does, exit your editor and move on to the next step.
If it doesn’t, update it to match. Then save the file, quit your editor, and verify the syntax of your configuration edits:
If you get an error, reopen the virtual host file and check for any typos or missing characters. Once your configuration file’s syntax is correct, reload Apache to load the new configuration:
Certbot can now find the correct VirtualHost block and update it.
Next, let’s update the firewall to allow HTTPS traffic.
Step 3 — Allowing HTTPS Through the Firewall
If you have the ufw firewall enabled, as recommended by the prerequisite guides, you’ll need to adjust the settings to allow for HTTPS traffic. Luckily, Apache registers a few profiles with ufw upon installation.
You can see the current setting by typing:
It will probably look like this, meaning that only HTTP traffic is allowed to the web server:
Status: active
To Action From
-- ------ ----
OpenSSH ALLOW Anywhere
Apache ALLOW Anywhere
OpenSSH (v6) ALLOW Anywhere (v6)
Apache (v6) ALLOW Anywhere (v6)
To additionally let in HTTPS traffic, allow the Apache Full profile and delete the redundant Apache profile allowance:
Your status should now look like this:
Status: active
To Action From
-- ------ ----
OpenSSH ALLOW Anywhere
Apache Full ALLOW Anywhere
OpenSSH (v6) ALLOW Anywhere (v6)
Apache Full (v6) ALLOW Anywhere (v6)
Next, let’s run Certbot and fetch our certificates.
Step 4 — Obtaining an SSL Certificate
Certbot provides a variety of ways to obtain SSL certificates through plugins. The Apache plugin will take care of reconfiguring Apache and reloading the config whenever necessary. To use this plugin, type the following:
This runs certbot with the --apache plugin, using -d to specify the names you’d like the certificate to be valid for.
If this is your first time running certbot, you will be prompted to enter an email address and agree to the terms of service. After doing so, certbot will communicate with the Let’s Encrypt server, then run a challenge to verify that you control the domain you’re requesting a certificate for.
If that’s successful, certbot will ask how you’d like to configure your HTTPS settings:
Please choose whether or not to redirect HTTP traffic to HTTPS, removing HTTP access.
-------------------------------------------------------------------------------
1: No redirect - Make no further changes to the webserver configuration.
2: Redirect - Make all requests redirect to secure HTTPS access. Choose this for
new sites, or if you're confident your site works on HTTPS. You can undo this
change by editing your web server's configuration.
-------------------------------------------------------------------------------
Select the appropriate number [1-2] then [enter] (press 'c' to cancel):
Select your choice then hit ENTER. The configuration will be updated, and Apache will reload to pick up the new settings. certbot will wrap up with a message telling you the process was successful and where your certificates are stored:
IMPORTANT NOTES:
- Congratulations! Your certificate and chain have been saved at:
/etc/letsencrypt/live/your_domain/fullchain.pem
Your key file has been saved at:
/etc/letsencrypt/live/your_domain/privkey.pem
Your cert will expire on 2018-07-23. To obtain a new or tweaked
version of this certificate in the future, simply run certbot again
with the "certonly" option. To non-interactively renew *all* of
your certificates, run "certbot renew"
- Your account credentials have been saved in your Certbot
configuration directory at /etc/letsencrypt. You should make a
secure backup of this folder now. This configuration directory will
also contain certificates and private keys obtained by Certbot so
making regular backups of this folder is ideal.
- If you like Certbot, please consider supporting our work by:
Donating to ISRG / Let's Encrypt: https://letsencrypt.org/donate
Donating to EFF: https://eff.org/donate-le
Your certificates are downloaded, installed, and loaded. Try reloading your website using https:// and notice your browser’s security indicator. It should indicate that the site is properly secured, usually with a green lock icon. If you test your server using the SSL Labs Server Test, it will get an A grade.
Let’s finish by testing the renewal process.
Step 5 — Verifying Certbot Auto-Renewal
The certbot package we installed takes care of renewals by including a renew script to /etc/cron.d, which is managed by a systemctl service called certbot.timer. This script runs twice a day and will automatically renew any certificate that’s within thirty days of expiration.
To check the status of this service and make sure it’s active and running, you can use:
You’ll get output similar to this:
● certbot.timer - Run certbot twice daily
Loaded: loaded (/lib/systemd/system/certbot.timer; enabled; vendor preset: enabled)
Active: active (waiting) since Tue 2020-04-28 17:57:48 UTC; 17h ago
Trigger: Wed 2020-04-29 23:50:31 UTC; 12h left
Triggers: ● certbot.service
Apr 28 17:57:48 fine-turtle systemd[1]: Started Run certbot twice daily.
To test the renewal process, you can do a dry run with certbot:
If you see no errors, you’re all set. When necessary, Certbot will renew your certificates and reload Apache to pick up the changes. If the automated renewal process ever fails, Let’s Encrypt will send a message to the email you specified, warning you when your certificate is about to expire.
Conclusion
In this tutorial, you installed the Let’s Encrypt client certbot, downloaded SSL certificates for your domain, configured Apache to use these certificates, and set up automatic certificate renewal. If you have further questions about using Certbot, their documentation is a good place to start.
How to Fix Windows and Linux Showing Different Times When Dual Booting
source: https://www.howtogeek.com/323390/how-to-fix-windows-and-linux-showing-different-times-when-dual-booting/
Make Linux Use Local Time
Making Linux use local time the same way Windows does is probably the best option. Windows does have a registry setting that forces it to store the time as UTC, but it reportedly isn’t well supported and can cause problems with some third-party applications that always assume the hardware clock is in local time. It’s also incompatible with Windows’ own Internet time-syncing service.
The steps to make your Linux system use local time can vary from Linux distribution to Linux distribution. However, on any Linux distribution with systemd, you can use the timedatectl command to make this change. This will work on modern versions of Ubuntu, Fedora, Red Hat, Debian, Mint, and other Linux distributions that use systemd.
To make this change, first open a Terminal window on your Linux system. Run the following command to put the real time clock on the motherboard into local time. Linux will store the time in local time, just like Windows does.
timedatectl set-local-rtc 1 --adjust-system-clock

To check your current settings, run:
timedatectl
If you see “RTC in local TZ: yes”, Linux is set to use the local time zone instead of UTC. The command warns you that this mode is not fully supported and can cause some problems when changing between time zones and with daylight savings time. However, this mode is probably better supported than the UTC option in Windows. If you dual-boot with Windows, Windows will handle daylight savings time for you.

If you ever want to undo this change, run the following command:
timedatectl set-local-rtc 0 --adjust-system-clock

Safest way to clean up boot partition – Ubuntu
source: https://gist.github.com/ipbastola/2760cfc28be62a5ee10036851c654600
Case I: if /boot is not 100% full and apt is working
1. Check the current kernel version
$ uname -r
It will shows the list like below:
3.19.0-64-generic
2. Remove the OLD kernels
2.a. List the old kernel
$ sudo dpkg --list 'linux-image*'|awk '{ if ($1=="ii") print $2}'|grep -v `uname -r`
You will get the list of images something like below:
linux-image-3.19.0-25-generic
linux-image-3.19.0-56-generic
linux-image-3.19.0-58-generic
linux-image-3.19.0-59-generic
linux-image-3.19.0-61-generic
linux-image-3.19.0-65-generic
linux-image-extra-3.19.0-25-generic
linux-image-extra-3.19.0-56-generic
linux-image-extra-3.19.0-58-generic
linux-image-extra-3.19.0-59-generic
linux-image-extra-3.19.0-61-generic
2.b. Now its time to remove old kernel one by one as
$ sudo apt-get purge linux-image-3.19.0-25-generic
$ sudo apt-get purge linux-image-3.19.0-56-generic
$ sudo apt-get purge linux-image-3.19.0-58-generic
$ sudo apt-get purge linux-image-3.19.0-59-generic
$ sudo apt-get purge linux-image-3.19.0-61-generic
$ sudo apt-get purge linux-image-3.19.0-65-generic
When you’re done removing the older kernels, you can run this to remove ever packages you won’t need anymore:
$ sudo apt-get autoremove
And finally you can run this to update grub kernel list:
$ sudo update-grub
Case II: Can’t Use apt i.e. /boot is 100% full
NOTE: this is only if you can’t use apt to clean up due to a 100% full /boot
1. Get the list of kernel images
Get the list of kernel images and determine what you can do without. This command will show installed kernels except the currently running one
$ sudo dpkg --list 'linux-image*'|awk '{ if ($1=="ii") print $2}'|grep -v `uname -r`
You will get the list of images somethign like below:
linux-image-3.19.0-25-generic
linux-image-3.19.0-56-generic
linux-image-3.19.0-58-generic
linux-image-3.19.0-59-generic
linux-image-3.19.0-61-generic
linux-image-3.19.0-65-generic
linux-image-extra-3.19.0-25-generic
linux-image-extra-3.19.0-56-generic
linux-image-extra-3.19.0-58-generic
linux-image-extra-3.19.0-59-generic
linux-image-extra-3.19.0-61-generic
2. Prepare Delete
Craft a command to delete all files in /boot for kernels that don’t matter to you using brace expansion to keep you sane. Remember to exclude the current and two newest kernel images. From above Example, it’s
sudo rm -rf /boot/*-3.19.0-{25,56,58,59,61,65}-*
3. Clean up what’s making apt grumpy about a partial install.
sudo apt-get -f install
4. Autoremove
Finally, autoremove to clear out the old kernel image packages that have been orphaned by the manual boot clean.
sudo apt-get autoremove
5. Update Grub
sudo update-grub
6. Now you can update, install packages
sudo apt-get updateHow to set up working X11 forwarding on WSL2
First: See and Install
Then:
Add the following to your ~/.bashrc:
export DISPLAY=$(awk '/nameserver / {print $2; exit}' /etc/resolv.conf 2>/dev/null):0
export LIBGL_ALWAYS_INDIRECT=1Enable Public Access on your X11 server for Windows.*
Add a separate inbound rule for TCP port 6000 to the windows firewall in order to allow WSL access to the X server, as described by the wsl-windows-toolbar-launcher people.
Source: https://stackoverflow.com/questions/61110603/how-to-set-up-working-x11-forwarding-on-wsl2
Windows Subsystem for Linux Installation Guide for Windows 10
source: https://docs.microsoft.com/en-us/windows/wsl/install-win10
Tutorial: https://youtu.be/47ksZLEDLFE
Install the Windows Subsystem for Linux
Before installing any Linux distros for WSL, you must ensure that the “Windows Subsystem for Linux” optional feature is enabled:
- Open PowerShell as Administrator and run:
Enable-WindowsOptionalFeature -Online -FeatureName Microsoft-Windows-Subsystem-Linux - Restart your computer when prompted.
Install your Linux Distribution of Choice
To download and install your preferred distro(s), you have three choices:
- Download and install from the Windows Store (see below)
- Download and install from the Command-Line/Script (read the manual installation instructions)
- Download and manually unpack and install (for Windows Server – instructions here)
Windows 10 Fall Creators Update and later: Install from the Microsoft Store
This section is for Windows build 16215 or later. Follow these steps to check your build.
- Open the Microsoft Store and choose your favorite Linux distribution.The following links will open the Windows store page for each distribution:
- From the distro’s page, select “Get”
Complete initialization of your distro
Now that your Linux distro is installed, you must initialize your new distro instance once, before it can be used.
How To Install Linux, Nginx, MySQL, PHP (LEMP stack) on Ubuntu 18.04
Introduction
The LEMP software stack is a group of software that can be used to serve dynamic web pages and web applications. This is an acronym that describes a Linux operating system, with an Nginx (pronounced like “Engine-X”) web server. The backend data is stored in the MySQL database and the dynamic processing is handled by PHP.
This guide demonstrates how to install a LEMP stack on an Ubuntu 18.04 server. The Ubuntu operating system takes care of the first requirement. We will describe how to get the rest of the components up and running.
Prerequisites
Before you complete this tutorial, you should have a regular, non-root user account on your server with sudo privileges. Set up this account by completing our initial server setup guide for Ubuntu 18.04.
Once you have your user available, you are ready to begin the steps outlined in this guide.
Step 1 – Installing the Nginx Web Server
In order to display web pages to our site visitors, we are going to employ Nginx, a modern, efficient web server.
All of the software used in this procedure will come from Ubuntu’s default package repositories. This means we can use the apt package management suite to complete the necessary installations.
Since this is our first time using apt for this session, start off by updating your server’s package index. Following that, install the server:
sudo apt update sudo apt install nginx
On Ubuntu 18.04, Nginx is configured to start running upon installation.
If you have the ufw firewall running, as outlined in the
initial setup guide, you will need to allow connections to Nginx. Nginx
registers itself with ufw upon installation, so the procedure is rather straightforward.
It is recommended that you enable the most restrictive profile that
will still allow the traffic you want. Since you haven’t configured SSL
for your server in this guide, you will only need to allow traffic on
port 80.
Enable this by typing:
sudo ufw allow 'Nginx HTTP'
You can verify the change by running:
sudo ufw status
This command’s output will show that HTTP traffic is allowed:
OutputStatus: active
To Action From
-- ------ ----
OpenSSH ALLOW Anywhere
Nginx HTTP ALLOW Anywhere
OpenSSH (v6) ALLOW Anywhere (v6)
Nginx HTTP (v6) ALLOW Anywhere (v6)
With the new firewall rule added, you can test if the server is up and running by accessing your server’s domain name or public IP address in your web browser.
If you do not have a domain name pointed at your server and you do not know your server’s public IP address, you can find it by running the following command:
ip addr show eth0 | grep inet | awk '{ print $2; }' | sed 's/\/.*$//'
This will print out a few IP addresses. You can try each of them in turn in your web browser.
As an alternative, you can check which IP address is accessible, as viewed from other locations on the internet:
curl -4 icanhazip.com
Type the address that you receive in your web browser and it will take you to Nginx’s default landing page:
http://server_domain_or_IP
If you see the above page, you have successfully installed Nginx.
Step 2 – Installing MySQL to Manage Site Data
Now that you have a web server, you need to install MySQL (a database management system) to store and manage the data for your site.
Install MySQL by typing:
sudo apt install mysql-server
The MySQL database software is now installed, but its configuration is not yet complete.
To secure the installation, MySQL comes with a script that will ask whether we want to modify some insecure defaults. Initiate the script by typing:
sudo mysql_secure_installation
This script will ask if you want to configure the VALIDATE PASSWORD PLUGIN.
Warning: Enabling this feature
is something of a judgment call. If enabled, passwords which don’t
match the specified criteria will be rejected by MySQL with an error.
This will cause issues if you use a weak password in conjunction with
software which automatically configures MySQL user credentials, such as
the Ubuntu packages for phpMyAdmin. It is safe to leave validation
disabled, but you should always use strong, unique passwords for
database credentials.
Answer Y for yes, or anything else to continue without enabling.
VALIDATE PASSWORD PLUGIN can be used to test passwords
and improve security. It checks the strength of password
and allows the users to set only those passwords which are
secure enough. Would you like to setup VALIDATE PASSWORD plugin?
Press y|Y for Yes, any other key for No:
If you’ve enabled validation, the script will also ask you to select a level of password validation. Keep in mind that if you enter 2 – for the strongest level – you will receive errors when attempting to set any password which does not contain numbers, upper and lowercase letters, and special characters, or which is based on common dictionary words.
There are three levels of password validation policy:
LOW Length >= 8
MEDIUM Length >= 8, numeric, mixed case, and special characters
STRONG Length >= 8, numeric, mixed case, special characters and dictionary file
Please enter 0 = LOW, 1 = MEDIUM and 2 = STRONG: 1
Next, you’ll be asked to submit and confirm a root password:
Please set the password for root here.
New password:
Re-enter new password:
For the rest of the questions, you should press Y and hit the ENTER
key at each prompt. This will remove some anonymous users and the test
database, disable remote root logins, and load these new rules so that
MySQL immediately respects the changes we have made.
Note that in Ubuntu systems running MySQL 5.7 (and later versions), the root MySQL user is set to authenticate using the auth_socket
plugin by default rather than with a password. This allows for some
greater security and usability in many cases, but it can also complicate
things when you need to allow an external program (e.g., phpMyAdmin) to
access the user.
If using the auth_socket plugin to access MySQL fits
with your workflow, you can proceed to Step 3. If, however, you prefer
to use a password when connecting to MySQL as root, you will need to switch its authentication method from auth_socket to mysql_native_password. To do this, open up the MySQL prompt from your terminal:
sudo mysql
Next, check which authentication method each of your MySQL user accounts use with the following command:
SELECT user,authentication_string,plugin,host FROM mysql.user;
Output+------------------+-------------------------------------------+-----------------------+-----------+
| user | authentication_string | plugin | host |
+------------------+-------------------------------------------+-----------------------+-----------+
| root | | auth_socket | localhost |
| mysql.session | *THISISNOTAVALIDPASSWORDTHATCANBEUSEDHERE | mysql_native_password | localhost |
| mysql.sys | *THISISNOTAVALIDPASSWORDTHATCANBEUSEDHERE | mysql_native_password | localhost |
| debian-sys-maint | *CC744277A401A7D25BE1CA89AFF17BF607F876FF | mysql_native_password | localhost |
+------------------+-------------------------------------------+-----------------------+-----------+
4 rows in set (0.00 sec)
In this example, you can see that the root user does in fact authenticate using the auth_socket plugin. To configure the root account to authenticate with a password, run the following ALTER USER command. Be sure to change password to a strong password of your choosing:
ALTER USER 'root'@'localhost' IDENTIFIED WITH mysql_native_password BY 'password';
Then, run FLUSH PRIVILEGES which tells the server to reload the grant tables and put your new changes into effect:
FLUSH PRIVILEGES;
Check the authentication methods employed by each of your users again to confirm that root no longer authenticates using the auth_socket plugin:
SELECT user,authentication_string,plugin,host FROM mysql.user;
Output+------------------+-------------------------------------------+-----------------------+-----------+
| user | authentication_string | plugin | host |
+------------------+-------------------------------------------+-----------------------+-----------+
| root | *3636DACC8616D997782ADD0839F92C1571D6D78F | mysql_native_password | localhost |
| mysql.session | *THISISNOTAVALIDPASSWORDTHATCANBEUSEDHERE | mysql_native_password | localhost |
| mysql.sys | *THISISNOTAVALIDPASSWORDTHATCANBEUSEDHERE | mysql_native_password | localhost |
| debian-sys-maint | *CC744277A401A7D25BE1CA89AFF17BF607F876FF | mysql_native_password | localhost |
+------------------+-------------------------------------------+-----------------------+-----------+
4 rows in set (0.00 sec)
You can see in this example output that the root MySQL user now authenticates using a password. Once you confirm this on your own server, you can exit the MySQL shell:
exit
Note: After configuring your root MySQL user to authenticate with a password, you’ll no longer be able to access MySQL with the sudo mysql command used previously. Instead, you must run the following:
mysql -u root -p
After entering the password you just set, you will see the MySQL prompt.
At this point, your database system is now set up and you can move on to installing PHP.
Step 3 – Installing PHP and Configuring Nginx to Use the PHP Processor
You now have Nginx installed to serve your pages and MySQL installed to store and manage your data. However, you still don’t have anything that can generate dynamic content. This is where PHP comes into play.
Since Nginx does not contain native PHP processing like some other web servers, you will need to install php-fpm, which stands for “fastCGI process manager”. We will tell Nginx to pass PHP requests to this software for processing.
Note: Depending on your cloud provider, you may need to add Ubuntu’s universe repository, which includes free and open-source software maintained by the Ubuntu community, before installing the php-fpm package. You can do this by typing:
sudo add-apt-repository universe
Install the php-fpm module along with an additional helper package, php-mysql,
which will allow PHP to communicate with your database backend. The
installation will pull in the necessary PHP core files. Do this by
typing:
sudo apt install php-fpm php-mysql
You now have all of the required LEMP stack components installed, but you still need to make a few configuration changes in order to tell Nginx to use the PHP processor for dynamic content.
This is done on the server block level (server blocks are similar to
Apache’s virtual hosts). To do this, open a new server block
configuration file within the /etc/nginx/sites-available/ directory. In this example, the new server block configuration file is named example.com, although you can name yours whatever you’d like:
sudo nano /etc/nginx/sites-available/example.com
By editing a new server block configuration file, rather than editing the default one, you’ll be able to easily restore the default configuration if you ever need to.
Add the following content, which was taken and slightly modified from the default server block configuration file, to your new server block configuration file: /etc/nginx/sites-available/example.com
server {
listen 80;
root /var/www/html;
index index.php index.html index.htm index.nginx-debian.html;
server_name example.com;
location / {
try_files $uri $uri/ =404;
}
location ~ \.php$ {
include snippets/fastcgi-php.conf;
fastcgi_pass unix:/var/run/php/php7.2-fpm.sock;
}
location ~ /\.ht {
deny all;
}
}
Here’s what each of these directives and location blocks do:
listen— Defines what port Nginx will listen on. In this case, it will listen on port80, the default port for HTTP.root— Defines the document root where the files served by the website are stored.index— Configures Nginx to prioritize serving files namedindex.phpwhen an index file is requested, if they’re available.server_name— Defines which server block should be used for a given request to your server. Point this directive to your server’s domain name or public IP address.location /— The first location block includes atry_filesdirective, which checks for the existence of files matching a URI request. If Nginx cannot find the appropriate file, it will return a 404 error.location ~ \.php$— This location block handles the actual PHP processing by pointing Nginx to thefastcgi-php.confconfiguration file and thephp7.2-fpm.sockfile, which declares what socket is associated withphp-fpm.location ~ /\.ht— The last location block deals with.htaccessfiles, which Nginx does not process. By adding thedeny alldirective, if any.htaccessfiles happen to find their way into the document root they will not be served to visitors.
After adding this content, save and close the file. Enable your new
server block by creating a symbolic link from your new server block
configuration file (in the /etc/nginx/sites-available/ directory) to the /etc/nginx/sites-enabled/ directory:
sudo ln -s /etc/nginx/sites-available/example.com /etc/nginx/sites-enabled/
Then, unlink the default configuration file from the /sites-enabled/ directory:
sudo unlink /etc/nginx/sites-enabled/default
Note: If you ever need to restore the default configuration, you can do so by recreating the symbolic link, like this:
sudo ln -s /etc/nginx/sites-available/default /etc/nginx/sites-enabled/
Test your new configuration file for syntax errors by typing:
sudo nginx -t
If any errors are reported, go back and recheck your file before continuing.
When you are ready, reload Nginx to make the necessary changes:
sudo systemctl reload nginx
This concludes the installation and configuration of your LEMP stack. However, it’s prudent to confirm that all of the components can communicate with one another.
Step 4 – Creating a PHP File to Test Configuration
Your LEMP stack should now be completely set up. You can test it to validate that Nginx can correctly hand .php files off to the PHP processor.
To do this, use your text editor to create a test PHP file called info.php in your document root:
sudo nano /var/www/html/info.php
Enter the following lines into the new file. This is valid PHP code that will return information about your server: /var/www/html/info.php
<?php
phpinfo();
When you are finished, save and close the file.
Now, you can visit this page in your web browser by visiting your server’s domain name or public IP address followed by /info.php:
http://your_server_domain_or_IP/info.php
You should see a web page that has been generated by PHP with information about your server:
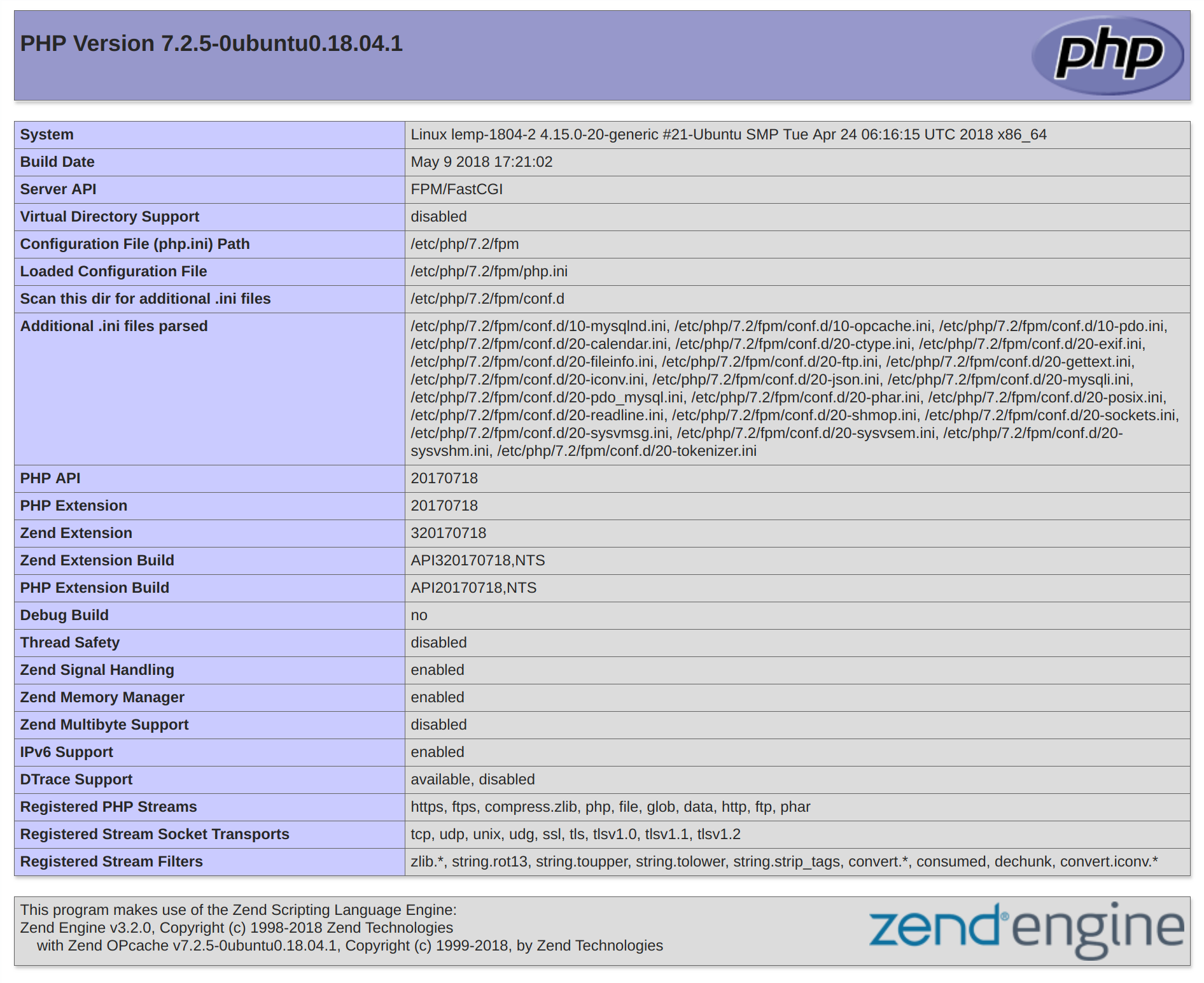
If you see a page that looks like this, you’ve set up PHP processing with Nginx successfully.
After verifying that Nginx renders the page correctly, it’s best to remove the file you created as it can actually give unauthorized users some hints about your configuration that may help them try to break in. You can always regenerate this file if you need it later.
For now, remove the file by typing:
sudo rm /var/www/html/info.php
With that, you now have a fully-configured and functioning LEMP stack on your Ubuntu 18.04 server.
Conclusion
A LEMP stack is a powerful platform that will allow you to set up and serve nearly any website or application from your server.
There are a number of next steps you could take from here. For example, you should ensure that connections to your server are secured. To this end, you could secure your Nginx installation with Let’s Encrypt. By following this guide, you will acquire a free TLS/SSL certificate for your server, allowing it to serve content over HTTPS.
Source: https://www.digitalocean.com/community/tutorials/how-to-install-linux-nginx-mysql-php-lemp-stack-ubuntu-18-04
How To Install Nginx on Ubuntu 18.04 [Quickstart]
Introduction
Nginx is one of the most popular web servers in the world and is responsible for hosting some of the largest and highest-traffic sites on the internet. It is more resource-friendly than Apache in most cases and can be used as a web server or reverse proxy.
In this guide, we’ll explain how to install Nginx on your Ubuntu 18.04 server. For a more detailed version of this tutorial, please refer to How To Install Nginx on Ubuntu 18.04.
Prerequisites
Before you begin this guide, you should have the following:
- An Ubuntu 18.04 server and a regular, non-root user with sudo privileges. Additionally, you will need to enable a basic firewall to block non-essential ports. You can learn how to configure a regular user account and set up a firewall by following our initial server setup guide for Ubuntu 18.04.
When you have an account available, log in as your non-root user to begin.
Step 1 – Installing Nginx
Because Nginx is available in Ubuntu’s default repositories, you can install it using the apt packaging system.
Update your local package index:
sudo apt update
Install Nginx:
sudo apt install nginx
Step 2 – Adjusting the Firewall
Check the available ufw application profiles:
sudo ufw app list
OutputAvailable applications:
Nginx Full
Nginx HTTP
Nginx HTTPS
OpenSSH
Let’s enable the most restrictive profile that will still allow the traffic you’ve configured, permitting traffic on port 80:
sudo ufw allow 'Nginx HTTP'
Verify the change:
sudo ufw status
OutputStatus: active
To Action From
-- ------ ----
OpenSSH ALLOW Anywhere
Nginx HTTP ALLOW Anywhere
OpenSSH (v6) ALLOW Anywhere (v6)
Nginx HTTP (v6) ALLOW Anywhere (v6)
Step 3 – Checking your Web Server
Check with the systemd init system to make sure the service is running by typing:
systemctl status nginx
Output● nginx.service - A high performance web server and a reverse proxy server
Loaded: loaded (/lib/systemd/system/nginx.service; enabled; vendor preset: enabled)
Active: active (running) since Fri 2018-04-20 16:08:19 UTC; 3 days ago
Docs: man:nginx(8)
Main PID: 2369 (nginx)
Tasks: 2 (limit: 1153)
CGroup: /system.slice/nginx.service
├─2369 nginx: master process /usr/sbin/nginx -g daemon on; master_process on;
└─2380 nginx: worker process
Access the default Nginx landing page to confirm that the software is running properly through your IP address:
http://your_server_ip
You should see the default Nginx landing page:
Step 4 – Setting Up Server Blocks (Recommended)
When using the Nginx web server, you can use server blocks (similar to virtual hosts in Apache) to encapsulate configuration details and host more than one domain from a single server. We will set up a domain called example.com, but you should replace this with your own domain name. To learn more about setting up a domain name with DigitalOcean, see our introduction to DigitalOcean DNS.
Create the directory for example.com, using the -p flag to create any necessary parent directories:
sudo mkdir -p /var/www/example.com/html
Assign ownership of the directory:
sudo chown -R $USER:$USER /var/www/example.com/html
The permissions of your web roots should be correct if you haven’t modified your umask value, but you can make sure by typing:
sudo chmod -R 755 /var/www/example.com
Create a sample index.html page using nano or your favorite editor:
nano /var/www/example.com/html/index.html
Inside, add the following sample HTML: /var/www/example.com/html/index.html
<html>
<head>
<title>Welcome to Example.com!</title>
</head>
<body>
<h1>Success! The example.com server block is working!</h1>
</body>
</html>
Save and close the file when you are finished.
Make a new server block at /etc/nginx/sites-available/example.com:
sudo nano /etc/nginx/sites-available/example.com
Paste in the following configuration block, updated for our new directory and domain name: /etc/nginx/sites-available/example.com
server {
listen 80;
listen [::]:80;
root /var/www/example.com/html;
index index.html index.htm index.nginx-debian.html;
server_name example.com www.example.com;
location / {
try_files $uri $uri/ =404;
}
}
Save and close the file when you are finished.
Enable the file by creating a link from it to the sites-enabled directory:
sudo ln -s /etc/nginx/sites-available/example.com /etc/nginx/sites-enabled/
Two server blocks are now enabled and configured to respond to requests based on their listen and server_name directives:
example.com: Will respond to requests forexample.comandwww.example.com.default: Will respond to any requests on port80that do not match the other two blocks.
To avoid a possible hash bucket memory problem that can arise from
adding additional server names, it is necessary to adjust a single value
in the /etc/nginx/nginx.conf file. Open the file:
sudo nano /etc/nginx/nginx.conf
Find the server_names_hash_bucket_size directive and remove the # symbol to uncomment the line:
/etc/nginx/nginx.conf
...
http {
...
server_names_hash_bucket_size 64;
...
}
...
Test for syntax errors:
sudo nginx -t
Restart Nginx to enable your changes:
sudo systemctl restart nginx
Nginx should now be serving your domain name. You can test this by navigating to http://example.com, where you should see something like this:
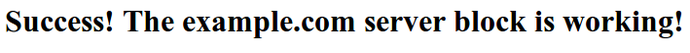
Conclusion
Now that you have your web server installed, you have many options for the type of content to serve and the technologies you want to use to create a richer experience.